Description
USB Blocker
USB Blocker is here to help you keep your computer safe from sneaky USB drives that might carry harmful stuff. Even though we mostly share data online these days, USB storage devices are still pretty popular. But without the right security, they can sneak in bad content without you even knowing it.
How USB Blocker Works
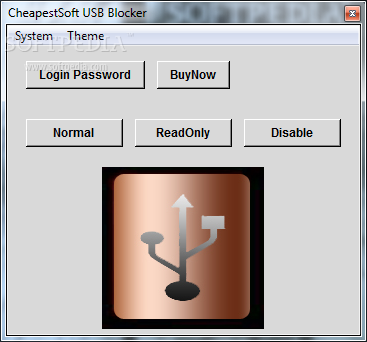
Once you get USB Blocker installed on your computer, you'll see just how easy it is to protect your portable devices. The app opens up in a compact window where you can find all its features clearly laid out. It might not win any design awards, but there are a few themes you can choose from to change things up a bit.
Getting Started
The first time you use the app, you'll need to log in with the default admin account. Don’t forget this password because if you do, those USB ports will be locked tight! No worries about USB mice or keyboards though; they’re not affected by this blocker.
Features and Limitations
One downside is that USB Blocker doesn’t show you a list of connected devices. Instead, it automatically targets all USB storage devices that plug in. You’ve got some options like making content read-only or disabling it altogether, but that’s about it.
User Experience Enhancements
I wish there were more ways to interact with the app, like accessing its lock features directly from a drive's menu or using hotkeys for quicker access. But here’s a tip: You can set up a hotkey for the app's shortcut in the Properties panel so that you can open it anytime!
The Bottom Line on USB Blocker
All in all, USB Blocker has good intentions and aims to make your device safer. However, it might leave you feeling a bit uneasy since any connected storage device gets targeted without showing which ones are blocked or keeping track of what happened during use. If you're looking for something simple yet effective for security against unwanted USB access, check out USB Blocker here!
Tags:
User Reviews for USB Blocker 1
-
for USB Blocker
USB Blocker offers basic protection by blocking USB storage devices, but lacks transparency in blocked devices and event logs.