Description
Trellix Stinger (formerly McAfee Stinger)
Formerly known as McAfee Stinger, Trellix Stinger relies on advanced security technologies to detect and remove threats on the host computer. It features rootkit scanning and leverages GTI File Reputation to analyze key locations on your machine and find potentially dangerous content and files.
Key Features:
- Advanced security technologies for threat detection
- Rootkit scanning capabilities
- GTI File Reputation analysis
- On-demand scans for viruses, rootkits, worms, and malware
- Customizable scan options
Technical Specifications:
- Price: FREE
- Publisher: Musarubra US LLC (Trellix)
- File: installer.exe
- Moderate system resource usage
Trellix Stinger is not a full-featured antivirus solution, but it can run alongside your security tool to ensure your system is free of threats from the list available in the "Advanced" menu. It is designed to detect and remove specific threats that have already reached your PC, including GameOver Zeus and CryptoLocker.
Scan and Clean:
The application scans the local device for specific threats and instantly tries to clean or quarantine infected files. You can easily customize the scan and select folders to analyze. A quarantine folder is automatically created to isolate infected files.
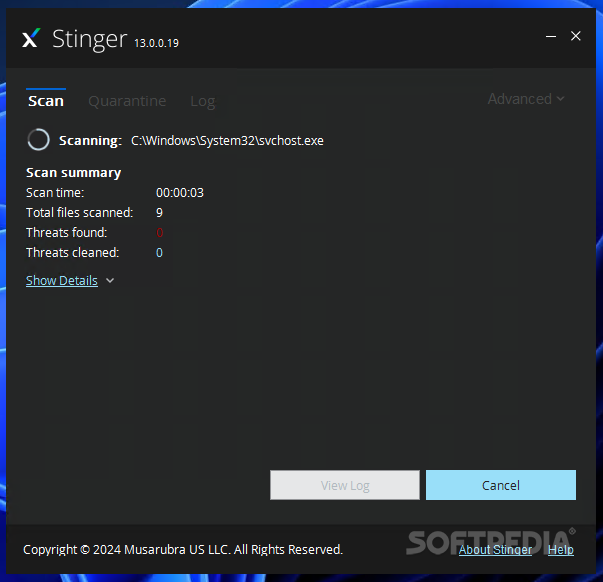
Scan Summary:
A summary is displayed as Trellix Stinger executes the task, showing the scan time and the number of files analyzed and threats cleaned. A scan log keeps track of Stinger's actions.
The application's system resource usage is moderate, even during a scan. However, it may default to analyzing all key locations in Windows, missing custom target locations.
Trellix Stinger is ideal for analyzing existing threats on your PC and removing them, but it does not offer real-time protection. Consider using it alongside a reliable security solution for full coverage.
Trellix Stinger (formerly McAfee Stinger) is available for free download at SoftPas.
User Reviews for Trellix Stinger (formerly McAfee Stinger) 1
-
for Trellix Stinger (formerly McAfee Stinger)
Trellix Stinger efficiently detects and removes threats. Suitable for on-demand scans, but lacks full antivirus protection. Moderate system resource usage.